OPC DA server configuration
Each instance of PcVue running on a computer host can expose an OPC DA server interface. For security reason, you can configure access control policies to define which PcVue host shall have the OPC DA server interface available.
An OPC DA server access control policy defines if and how the server interacts with OPC clients, including authentication, browsing, logging, and communication handling. These policies ensure secure and efficient data exchange by managing how OPC DA client permissions enforcement, write operations, and error-handling are performed.
This topic covers how to configure an OPC DA access control list.
By default, the OPC DA server interface is only accessible to PcVue built-in components on all stations, in particular to the HDS for data archiving purpose.
If you are using third party OPC clients, add a policy for the list of PcVue servers these OPC clients will connect to. We recommend you to select OPC clients that support OPC security and turn authentication on.
Configuring an access control policy
-
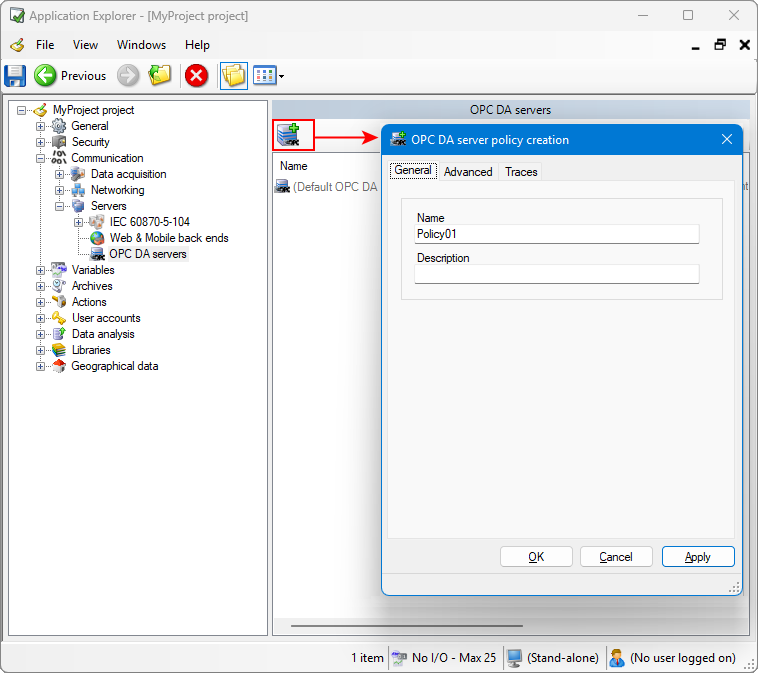
Open the Application Explorer and expand Communication then Servers nodes.
-
Select the OPC DA servers and in the right pane, click Add an OPC DA server policy. The Policy creation dialog opens.
 Show picture
Show picture -
Enter a name and (Optional) a description.
-
Select the Advanced tab and define the advanced properties.
Advanced properties
- Access control:
- Exclusive - If ticked, restricts access to PcVue built-in components, including the HDS.
- Turn on authentication - If ticked, requires OPC clients to authenticate before interaction. To enable authentication, you must configure one or more user accounts with a Name, Password, and Browsing levels in the User accounts configuration. Each variable have an assigned browsing level, which can be set in the Advanced dialog of the variable's configuration. Refer to How to configure a user for more information.
- OPC clients can only see variables that match the browsing levels of the logged-in account.
- Write access is granted only if the account's command permissions match the variable's command level.
- OPC client actions, including logon/logoff and write operations, can be logged.
- Turn off authentication - If ticked, allows OPC clients to interact without authentication.
- Allowed services:
- Writes - If ticked, allows an OPC client to write values via the PcVue's OPC server.
- Browsing - If ticked, allows an OPC client to browse PcVue's address space.
- Log user actions:
- Writes - If ticked, logs all write requests to PcVue from an OPC client.
- Logon/logoff - If ticked, logs the action of an OPC client logging on or off.
- Address space browsing:
- Display properties - If ticked, variable's properties (description, Domain, Nature etc.) are exposed in the address space (in addition to the variables themselves).
- Interoperability issues:
- Ignore client callback errors - If ticked, sets the action to be taken when the OPC server notifies an OPC client that a function call has failed.
If unticked, the result code is treated as a communication failure and the OPC connection is reset. The client then has to terminate the current connection and make a new one.
If ticked, the result code is ignored and the communication continues with the current connection. - Purge pending OnDataChange - If ticked, the OPC Server will purge data buffers if the subscribed OPC client failed to consume the data.
- Networking:
- Servers - Name of the servers list to which the access control policy applies. The OPC DA server will be exposed as defined by the policy on all stations belonging to the selected list. Refer to the topic How to configure station lists to learn more.
A browsing level can also be assigned to a variable's extended attributes and the simulation properties. The browsing level assigned to a particular extended attribute is global - that is, it affects that attribute for all variables.
With authentication is enabled:
If an OPC client does not log on, it inherits the browsing and command levels from the DEFPROFILE.
Disabling authentication or logging weakens security and increases the risk of unauthorized access. Ensure changes comply with your organization's security policies.
When using authentication, commands from the OPC client can be logged as if they were commands from a user logged onto PcVue.
The default policy applies to the OPC DA server of PcVue stations for which no other access control policy matches.
Activate traces
The traces in the OPC DA server access control policy are activated once you click Apply after having configured the general and advanced properties.
The following are some of the traces you can activate:
- Trace 1: General - Logs data related to the overall OPC DA server activity, including client connections, disconnections, and configuration changes.
- Trace 4: Full details - Provide in-depth details for all currently active logs data.
- Trace 5: IOPCCommon - Logs data related to basic OPC connection setup, such as locale and setting client’s name.
- Trace 6: IOPCServer - Logs data on general OPC server operations, including namespace handling and group creation.
- Trace 7: IOPCServer::GetStatus() - Logs status requests from OPC clients to monitor server health.
- Trace 8 : IConnectionPointContainer - Logs request from OPC clients and groups to obtain valid connection points, including for IOPCShutdown.
- Trace 9 : IOPCItemProperties - Logs requests for item properties such as descriptions, data types etc.
- Trace 10 : IOPCBrowse ServerAddressSpace - Logs browsing operations in the OPC server’s address space.
- Trace 11: IOPCSecurityPrivate/IOPCSecurityNT - Logs data related to the authentication and security-related operations.
- Trace 13: IOPCGroupStateMgt - Logs changes in OPC group state, including creation, deletion, and updates.
- Trace 14 : IOPCSyncIO - Logs synchronous read and write operations between OPC clients and the server.
- Trace 15: IOPCAsyncIO - Logs asynchronous data access operations relying on IDataObject between OPC clients and the server.
- Trace 16 : IOPCAsyncIO2 - Logs asynchronous data access operations relying on IConnectionPointContainer and IOPCDataCallback between OPC clients and the server.
- Trace 17 : IOPCItemMgt - Logs client requests to add or remove items in an OPC group.
- Trace 18: IConnectionPointContainer - Logs asynchronous data access operations relying on IConnectionPointContainer between OPC clients and the server.
- Trace 19: IDataObject - Logs requests related to connection and data using the IDataObject interface.
- Trace 21: IOPCGroupStateMgt2 - Logs additional changes on OPC group state (as per IOPCGroupStateMgt) and OPC group keep-alive related requests.
- Trace 29: IOPCDataCallback - Logs data change notifications sent from the server to OPC clients.
- Trace 30: IOPCShutdown - Logs data related to the shutdown events and notifications sent to OPC clients.
- Trace 31: IAdviseSink - Logs OPC server interfaces notifications sent to the OPC clients.
- Trace 32: IEnumOPCItemAttributes - Logs enumeration of item attributes requested by OPC clients.