Security overview
The Security node in the Application Explorer provides the possibility to reference security certificates that enable the secure exchange of information between PcVue and other components it communicates with. Certificates behind the Security node are references to actual certificates, designed to abstract the actual certificate's name and characteristics to other PcVue features. You can reference a certificate that already exists, or create a new one and reference it.
At the time of writing this topic, security certificates you reference on the Security node are only used for the OPC UA client driver.
PcVue's PKI
For applications to interact and exchange data with one another, a trust relation between them must be established when a Security Policy different than None is enforced.
PcVue provides a built-in PKI configured through a local certificate store which allows to manage certificates. It is located in the \PKI root directory, at the same level as the \BIN folder and is organized as follows:
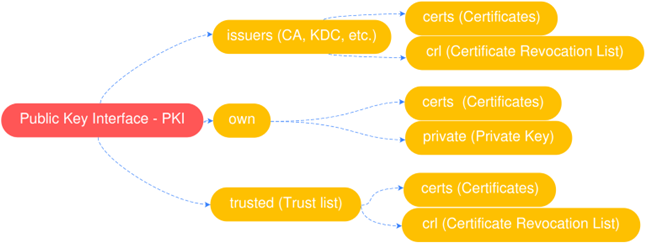
The interaction with this folder structure depends on how the trust relation is built between the applications: using CA-Signed or Self-Signed certificates.
It is important to note that in both situations the \own folders contains:
-
The application instance certificate holding the public key in the \certs folder.
-
The application private key hosted in the \private folder.
Security certificates
The use of a CA entity relies on the principle of Trusted Third Parties (TTP). This TTP is an entity which facilitates the establishment of trust between two entities by trusting a common third one (and its judgments, for instance if it revokes a party’s certificate), here the CA.
If PcVue needs to communicate with a given server for instance, it only needs to trust the CA (TTP) trusted by that given server, by adding the CA certificates into its Trust List (reciprocally the server must trust the same CA). Logically, if the CA certificate is not copied to the Trust List, PcVue’s PKI will fail to authenticate the server and it will not be possible to establish a secure channel.
Trust establishment differs if the CA involved in the infrastructure are numerous and hierarchically linked. The CA with the highest hierarchy level is considered the TTP and the root of this chain, hence it is often referred as a “trust anchor”.
Refer to the topic How to create a security certificate to learn more about certificate configuration.
Self-signed certificates
PcVue's security feature also provides the possibility to create self-signed certificates. In this case, the client and server within the PKI system cannot use a TTP (CA) as a common entity to establish a trust relation. As no TTP can sign the client and server certificates, there are no guaranties on those certificates' origins, leaving the identities of the applications uncertain. This low level security set-up should only be used for specific situations such as test phase, PoC etc. It is strongly discouraged for deployment in production.